Some cryptocurrencies share a blockchain, even though other cryptocurrencies run by themselves individual blockchains.
These risk actors were then in a position to steal AWS session tokens, the momentary keys that enable you to request short-term credentials towards your employer?�s AWS account. By hijacking active tokens, the attackers have been able to bypass MFA controls and attain entry to Harmless Wallet ?�s AWS account. By timing their efforts to coincide Using the developer?�s ordinary operate hours, In addition they remained undetected right up until the particular heist.
Together with US regulation, cooperation and collaboration?�domestically and internationally?�is essential, significantly presented the restricted possibility that exists to freeze or Recuperate stolen money. Successful coordination concerning field actors, government organizations, and regulation enforcement need to be included in any attempts to bolster the security of copyright.
The trades may sense repetitive, nevertheless they've made an effort to add a lot more tracks later while in the application (i such as Futures and choices). That is it. Over-all It is a fantastic app that produced me trade every day for two mo. Leverage is straightforward and boosts are good. The bugs are rare and skip capable.
Overall, building a protected copyright field will require clearer regulatory environments that organizations can properly function in, modern plan alternatives, higher security benchmarks, and formalizing international and domestic partnerships.
Hi there! We noticed your evaluate, and we wanted to check how we might assist you. Would you give us a lot more particulars about your inquiry?
enable it to be,??cybersecurity steps may possibly grow to be an afterthought, especially when providers lack the resources or staff for this sort of actions. The trouble isn?�t one of a kind to People new to business; nonetheless, even very well-established corporations might Permit cybersecurity slide to your wayside or might absence the training to be aware of the promptly evolving danger landscape.
As soon as you?�ve created and funded a copyright.US account, you?�re just seconds far from creating your initial copyright buy.
Several argue that regulation powerful for securing banking companies is considerably less successful during the copyright Area a result of the marketplace?�s decentralized nature. copyright requires a lot more security rules, but it also wants new methods that bear in mind its distinctions from fiat fiscal establishments.
On February 21, 2025, copyright exchange copyright executed what was imagined to be described as a schedule transfer of consumer money from their cold wallet, a more secure offline wallet utilized for long run storage, to their heat wallet, an internet-related wallet which offers far more accessibility than chilly wallets when maintaining far more security than very hot wallets.
Policy remedies need to put far more emphasis on educating market actors around important threats in copyright plus the part of cybersecurity while also incentivizing bigger protection website specifications.
Since the risk actors engage With this laundering method, copyright, law enforcement, and associates from over the marketplace keep on to actively perform to recover the funds. However, the timeframe where by cash may be frozen or recovered moves fast. In the laundering method you will discover a few most important levels wherever the resources is often frozen: when it?�s exchanged for BTC; when It can be exchanged for any stablecoin, or any copyright with its worth hooked up to steady belongings like fiat currency; or when It really is cashed out at exchanges.
Bitcoin takes advantage of the Unspent Transaction Output (UTXO) product, corresponding to transactions with physical income where by Every single individual Invoice would want to become traced. On other hand, Ethereum takes advantage of an account design, akin to a banking account by using a functioning balance, which happens to be additional centralized than Bitcoin.
It boils right down to a supply chain compromise. To carry out these transfers securely, Every transaction needs many signatures from copyright employees, referred to as a multisignature or multisig course of action. To execute these transactions, copyright depends on Harmless Wallet , a third-occasion multisig System. Before in February 2025, a developer for Safe and sound Wallet fell for your social engineering assault, and his workstation was compromised by malicious actors.
six. Paste your deposit handle as the location deal with while in the wallet you will be initiating the transfer from
??Moreover, Zhou shared which the hackers begun applying BTC and ETH mixers. Given that the title implies, mixers mix transactions which further inhibits blockchain analysts??power to observe the money. Adhering to the use of mixers, these North Korean operatives are leveraging peer to see (P2P) suppliers, platforms facilitating the direct buy and selling of copyright from a person consumer to another.}
 Danny Tamberelli Then & Now!
Danny Tamberelli Then & Now! Haley Joel Osment Then & Now!
Haley Joel Osment Then & Now! Ralph Macchio Then & Now!
Ralph Macchio Then & Now!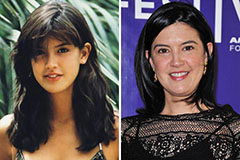 Phoebe Cates Then & Now!
Phoebe Cates Then & Now! Megyn Kelly Then & Now!
Megyn Kelly Then & Now!